NMAP – NSE(Nmap Script Engine)
NMAP ---> 스캐너 : 네트워크 Discovery ---> Host ---> port scan
NMAP + 추가 모듈 (확장기능)
NSE 분류
1.Network discovery
2.More Sophisticated and accurate OS version detction
기본 NMAP과 비교하여 정밀한 탐지가 가능하다.
3. Vulnerability Detection
4. Backdoor Detection
5. Vulnerability Exploitation ---> #취약점 공격해서 침투테스트까지 가능하다.
NMAP + Script : 정교하거나 추가된 기능을 사용할 수 있다.
Script ---> NMAP에서 사용하는 script의 확장자 : nse
현재 설치된 운영체제에서 nse 파일을 찾아보자.
find / -name *.nse #파일을 찾음.
locate *.nse #파일의 위치를 찾아준다.
nse 스크립트 파일의 위치 : /usr/share/nmap/scripts/
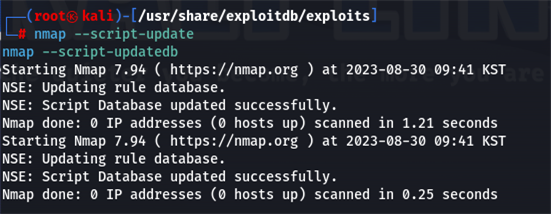
nmap의 스크립트 파일은 업데이트가 가능하다.
nmap --script-update
nmap --script-updatedb
dns-brute.nse ===> 딕셔너리 어택 : 대상 : DNS #루비 코드로 작성되어 있다.
--->dns enum 공격
사용법 : 기본 NMAP
nmap –p 53 —script dns-brute.nse [공격대상 dns서버]
#툴마다 기능이 다르기 때문에 다양하게 사용하고 비교하자.
www.ubiedu.co.kr / 14.36.28.250
--> 버츄얼 호스팅이 되어 있다.
--> 도메인 주소는 https 보안이 되어 있다.
--> IP로 접속 하였을때는 보안이 취약할 수도 있다.
대상 사이트가 웹 서버일 때
http 페이지를 식별한다.
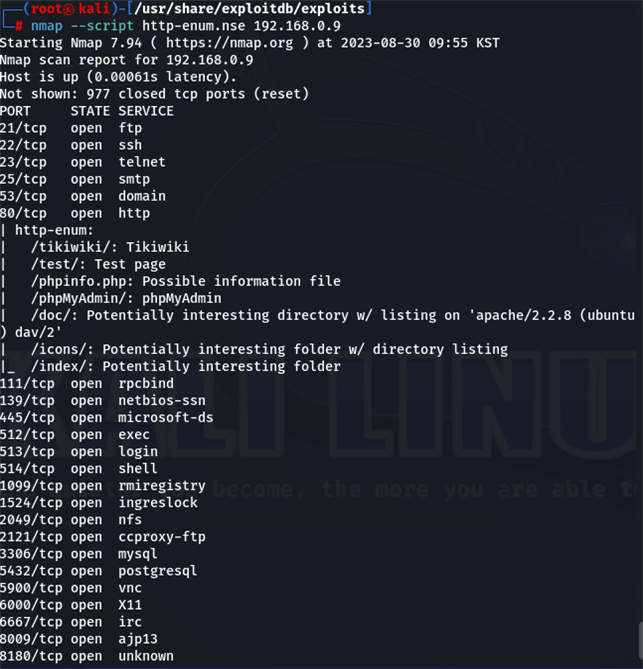
http-enum.nse
nmap —script http-enum.nse 192.168.0.9
스캔 완료 화면
스캐너 : vulscan.nse #취약점 탐색
기본 NSE에는 없음 --> 추가 다운로드 필요
cd /usr/share/nmap/scripts/
mkdir addon
cd addon
wget https://github.com/vulnersCom/nmap-vulners/archive/refs/heads/master.zip
unzip master.zip

nmap-vulners-master/vulners.nse 획득
https://podman.io/ : pod를 적게 사용하는 경우
kubernetes ---> 이름이 갈다. ---> k9s ---> : 구버네티스 오케이스트레이션 프로그램 자체가 무겁다.
-ubernete
==> micro Kuvernetes
--> k9s
웹서버 취약점 분석 (CVE 취약점 분석)
nmap –sV –p 80 —script=nmap-vulners-master/vulners.nse
msfconsole과 연계 가능 #CVE코드 검색
msfconsole
search [CVE코드]
ls | grep ssh

ssh-brute.nse : ssh 서비스에 대한 브루트포스를 진행
필수조건 : user.lst
pw.lst
기본으로 만들어 쓰자.
echo “aaa
bbb
ccc“ > user.lst
echo “aaa
bbb
ccc“ > pw.lst
공격코드
nmap -n -p22 --script ssh-brute.nse --script-args userdb=user.lst,passdb=pw.lst 192.168.0.9

부르트포스 날림
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# nmap -n -p22 --script ssh-brute.nse --script-args userdb=user.lst,passdb=pw.lst 192.168.0.9 Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-30 10:42 KST NSE: [ssh-brute] Trying username/password pair: aaa:aaa NSE: [ssh-brute] Trying username/password pair: bbb:bbb NSE: [ssh-brute] Trying username/password pair: ccc:ccc NSE: [ssh-brute] Trying username/password pair: bbb:aaa NSE: [ssh-brute] Trying username/password pair: ccc:aaa NSE: [ssh-brute] Trying username/password pair: aaa:bbb NSE: [ssh-brute] Trying username/password pair: ccc:bbb NSE: [ssh-brute] Trying username/password pair: aaa:ccc NSE: [ssh-brute] Trying username/password pair: bbb:ccc Nmap scan report for 192.168.0.9 Host is up (0.00024s latency). |
SMB 유저 탐색
smb-enum.nse
nmap –n –p139,445 --script=smb-enum-users --script-args=smbuername=“test”, \smbpassword=“asd123!@”,samronly 192.168.0.9
firewalk.nse (방화벽에 적용된 룰 확인) +@
대상 서버에 설정되어 있는 방화벽 설정값을 확인 ---> port scan
추가 기능 --> traceroute : 경로 확인
nmap --script firewalk.nse --traceroute 192.168.0.9

myspl-info.nse
mysql정보와 버전 상태 // --> password salt : 소금(salt) ---> 패스워드를 알아내기 위한 키 (패스워드)
nmap —script=mysql-info.nse –sV –sC 192.168.0.9

https://st-lab.tistory.com/100
nse파일
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# ls | grep http http-adobe-coldfusion-apsa1301.nse http-affiliate-id.nse http-apache-negotiation.nse http-apache-server-status.nse http-aspnet-debug.nse http-auth-finder.nse http-auth.nse http-avaya-ipoffice-users.nse http-awstatstotals-exec.nse http-axis2-dir-traversal.nse http-backup-finder.nse http-barracuda-dir-traversal.nse http-bigip-cookie.nse http-brute.nse http-cakephp-version.nse http-chrono.nse http-cisco-anyconnect.nse http-coldfusion-subzero.nse http-comments-displayer.nse http-config-backup.nse http-cookie-flags.nse http-cors.nse http-cross-domain-policy.nse http-csrf.nse http-date.nse http-default-accounts.nse http-devframework.nse http-dlink-backdoor.nse http-dombased-xss.nse http-domino-enum-passwords.nse http-drupal-enum-users.nse http-drupal-enum.nse http-enum.nse http-errors.nse http-exif-spider.nse http-favicon.nse http-feed.nse http-fetch.nse http-fileupload-exploiter.nse http-form-brute.nse http-form-fuzzer.nse http-frontpage-login.nse http-generator.nse http-git.nse http-gitweb-projects-enum.nse http-google-malware.nse http-grep.nse http-headers.nse http-hp-ilo-info.nse http-huawei-hg5xx-vuln.nse http-icloud-findmyiphone.nse http-icloud-sendmsg.nse http-iis-short-name-brute.nse http-iis-webdav-vuln.nse http-internal-ip-disclosure.nse http-joomla-brute.nse http-jsonp-detection.nse http-litespeed-sourcecode-download.nse http-ls.nse http-majordomo2-dir-traversal.nse http-malware-host.nse http-mcmp.nse http-method-tamper.nse http-methods.nse http-mobileversion-checker.nse http-ntlm-info.nse http-open-proxy.nse http-open-redirect.nse http-passwd.nse http-php-version.nse http-phpmyadmin-dir-traversal.nse http-phpself-xss.nse http-proxy-brute.nse http-put.nse http-qnap-nas-info.nse http-referer-checker.nse http-rfi-spider.nse http-robots.txt.nse http-robtex-reverse-ip.nse http-robtex-shared-ns.nse http-sap-netweaver-leak.nse http-security-headers.nse http-server-header.nse http-shellshock.nse http-sitemap-generator.nse http-slowloris-check.nse http-slowloris.nse http-sql-injection.nse http-stored-xss.nse http-svn-enum.nse http-svn-info.nse http-title.nse http-tplink-dir-traversal.nse http-trace.nse http-traceroute.nse http-trane-info.nse http-unsafe-output-escaping.nse http-useragent-tester.nse http-userdir-enum.nse http-vhosts.nse http-virustotal.nse http-vlcstreamer-ls.nse http-vmware-path-vuln.nse http-vuln-cve2006-3392.nse http-vuln-cve2009-3960.nse http-vuln-cve2010-0738.nse http-vuln-cve2010-2861.nse http-vuln-cve2011-3192.nse http-vuln-cve2011-3368.nse http-vuln-cve2012-1823.nse http-vuln-cve2013-0156.nse http-vuln-cve2013-6786.nse http-vuln-cve2013-7091.nse http-vuln-cve2014-2126.nse http-vuln-cve2014-2127.nse http-vuln-cve2014-2128.nse http-vuln-cve2014-2129.nse http-vuln-cve2014-3704.nse http-vuln-cve2014-8877.nse http-vuln-cve2015-1427.nse http-vuln-cve2015-1635.nse http-vuln-cve2017-1001000.nse http-vuln-cve2017-5638.nse http-vuln-cve2017-5689.nse http-vuln-cve2017-8917.nse http-vuln-misfortune-cookie.nse http-vuln-wnr1000-creds.nse http-waf-detect.nse http-waf-fingerprint.nse http-webdav-scan.nse http-wordpress-brute.nse http-wordpress-enum.nse http-wordpress-users.nse http-xssed.nse https-redirect.nse ip-https-discover.nse membase-http-info.nse riak-http-info.nse ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# |
http 관련 스크립트를 전부 실행
nmap –p 80 –sV —script “http-*” 192.168.0.9
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# ls | grep "http-" http-adobe-coldfusion-apsa1301.nse http-affiliate-id.nse http-apache-negotiation.nse http-apache-server-status.nse http-aspnet-debug.nse http-auth-finder.nse http-auth.nse http-avaya-ipoffice-users.nse http-awstatstotals-exec.nse http-axis2-dir-traversal.nse http-backup-finder.nse http-barracuda-dir-traversal.nse http-bigip-cookie.nse http-brute.nse http-cakephp-version.nse http-chrono.nse http-cisco-anyconnect.nse http-coldfusion-subzero.nse http-comments-displayer.nse http-config-backup.nse http-cookie-flags.nse http-cors.nse http-cross-domain-policy.nse http-csrf.nse http-date.nse http-default-accounts.nse http-devframework.nse http-dlink-backdoor.nse http-dombased-xss.nse http-domino-enum-passwords.nse http-drupal-enum-users.nse http-drupal-enum.nse http-enum.nse http-errors.nse http-exif-spider.nse http-favicon.nse http-feed.nse http-fetch.nse http-fileupload-exploiter.nse http-form-brute.nse http-form-fuzzer.nse http-frontpage-login.nse http-generator.nse http-git.nse http-gitweb-projects-enum.nse http-google-malware.nse http-grep.nse http-headers.nse http-hp-ilo-info.nse http-huawei-hg5xx-vuln.nse http-icloud-findmyiphone.nse http-icloud-sendmsg.nse http-iis-short-name-brute.nse http-iis-webdav-vuln.nse http-internal-ip-disclosure.nse http-joomla-brute.nse http-jsonp-detection.nse http-litespeed-sourcecode-download.nse http-ls.nse http-majordomo2-dir-traversal.nse http-malware-host.nse http-mcmp.nse http-method-tamper.nse http-methods.nse http-mobileversion-checker.nse http-ntlm-info.nse http-open-proxy.nse http-open-redirect.nse http-passwd.nse http-php-version.nse http-phpmyadmin-dir-traversal.nse http-phpself-xss.nse http-proxy-brute.nse http-put.nse http-qnap-nas-info.nse http-referer-checker.nse http-rfi-spider.nse http-robots.txt.nse http-robtex-reverse-ip.nse http-robtex-shared-ns.nse http-sap-netweaver-leak.nse http-security-headers.nse http-server-header.nse http-shellshock.nse http-sitemap-generator.nse http-slowloris-check.nse http-slowloris.nse http-sql-injection.nse http-stored-xss.nse http-svn-enum.nse http-svn-info.nse http-title.nse http-tplink-dir-traversal.nse http-trace.nse http-traceroute.nse http-trane-info.nse http-unsafe-output-escaping.nse http-useragent-tester.nse http-userdir-enum.nse http-vhosts.nse http-virustotal.nse http-vlcstreamer-ls.nse http-vmware-path-vuln.nse http-vuln-cve2006-3392.nse http-vuln-cve2009-3960.nse http-vuln-cve2010-0738.nse http-vuln-cve2010-2861.nse http-vuln-cve2011-3192.nse http-vuln-cve2011-3368.nse http-vuln-cve2012-1823.nse http-vuln-cve2013-0156.nse http-vuln-cve2013-6786.nse http-vuln-cve2013-7091.nse http-vuln-cve2014-2126.nse http-vuln-cve2014-2127.nse http-vuln-cve2014-2128.nse http-vuln-cve2014-2129.nse http-vuln-cve2014-3704.nse http-vuln-cve2014-8877.nse http-vuln-cve2015-1427.nse http-vuln-cve2015-1635.nse http-vuln-cve2017-1001000.nse http-vuln-cve2017-5638.nse http-vuln-cve2017-5689.nse http-vuln-cve2017-8917.nse http-vuln-misfortune-cookie.nse http-vuln-wnr1000-creds.nse http-waf-detect.nse http-waf-fingerprint.nse http-webdav-scan.nse http-wordpress-brute.nse http-wordpress-enum.nse http-wordpress-users.nse http-xssed.nse membase-http-info.nse riak-http-info.nse ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# |
NMAP ---> 스캐너 : 네트워크 Discovery ---> Host ---> port scan
NMAP + 추가 모듈 (확장기능)
NSE 분류
Network discovery
More Sophisticated and accurate OS version detction
기본 NMAP과 비교하여 정밀한 탐지가 가능하다.
3. Vulnerability Detection
4. Backdoor Detection
5. Vulnerability Exploitation ---> #취약점 공격해서 침투테스트까지 가능하다.
NMAP + Script : 정교하거나 추가된 기능을 사용할 수 있다.
Script ---> NMAP에서 사용하는 script의 확장자 : nse
현재 설치된 운영체제에서 nse 파일을 찾아보자.
find / -name *.nse #파일을 찾음.
locate *.nse #파일의 위치를 찾아준다.
nse 스크립트 파일의 위치 : /usr/share/nmap/scripts/
nmap의 스크립트 파일은 업데이트가 가능하다.
nmap --script-update
nmap --script-updatedb
dns-brute.nse ===> 딕셔너리 어택 : 대상 : DNS #루비 코드로 작성되어 있다.
--->dns enum 공격
사용법 : 기본 NMAP
nmap –p 53 —script dns-brute.nse [공격대상 dns서버]
#툴마다 기능이 다르기 때문에 다양하게 사용하고 비교하자.
www.ubiedu.co.kr / 14.36.28.250
--> 버츄얼 호스팅이 되어 있다.
--> 도메인 주소는 https 보안이 되어 있다.
--> IP로 접속 하였을때는 보안이 취약할 수도 있다.
대상 사이트가 웹 서버일 때
http 페이지를 식별한다.
http-enum.nse
nmap —script http-enum.nse 192.168.0.9
스캔 완료 화면
스캐너 : vulscan.nse #취약점 탐색
기본 NSE에는 없음 --> 추가 다운로드 필요
cd /usr/share/nmap/scripts/
mkdir addon
cd addon
wget https://github.com/vulnersCom/nmap-vulners/archive/refs/heads/master.zip
unzip master.zip
nmap-vulners-master/vulners.nse 획득
https://podman.io/ : pod를 적게 사용하는 경우
kubernetes ---> 이름이 갈다. ---> k9s ---> : 구버네티스 오케이스트레이션 프로그램 자체가 무겁다.
-ubernete
==> micro Kuvernetes
--> k9s
웹서버 취약점 분석 (CVE 취약점 분석)
nmap –sV –p 80 —script=nmap-vulners-master/vulners.nse
msfconsole과 연계 가능 #CVE코드 검색
msfconsole
search [CVE코드]
ls | grep ssh
ssh-brute.nse : ssh 서비스에 대한 브루트포스를 진행
필수조건 : user.lst
pw.lst
기본으로 만들어 쓰자.
echo “aaa
bbb
ccc“ > user.lst
echo “aaa
bbb
ccc“ > pw.lst
공격코드
nmap -n -p22 --script ssh-brute.nse --script-args userdb=user.lst,passdb=pw.lst 192.168.0.9
부르트포스 날림
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# nmap -n -p22 --script ssh-brute.nse --script-args userdb=user.lst,passdb=pw.lst 192.168.0.9 Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-30 10:42 KST NSE: [ssh-brute] Trying username/password pair: aaa:aaa NSE: [ssh-brute] Trying username/password pair: bbb:bbb NSE: [ssh-brute] Trying username/password pair: ccc:ccc NSE: [ssh-brute] Trying username/password pair: bbb:aaa NSE: [ssh-brute] Trying username/password pair: ccc:aaa NSE: [ssh-brute] Trying username/password pair: aaa:bbb NSE: [ssh-brute] Trying username/password pair: ccc:bbb NSE: [ssh-brute] Trying username/password pair: aaa:ccc NSE: [ssh-brute] Trying username/password pair: bbb:ccc Nmap scan report for 192.168.0.9 Host is up (0.00024s latency). |
SMB 유저 탐색
smb-enum.nse
nmap –n –p139,445 --script=smb-enum-users --script-args=smbuername=“test”, \smbpassword=“asd123!@”,samronly 192.168.0.9
firewalk.nse (방화벽에 적용된 룰 확인) +@
대상 서버에 설정되어 있는 방화벽 설정값을 확인 ---> port scan
추가 기능 --> traceroute : 경로 확인
nmap --script firewalk.nse --traceroute 192.168.0.9
myspl-info.nse
mysql정보와 버전 상태 // --> password salt : 소금(salt) ---> 패스워드를 알아내기 위한 키 (패스워드)
nmap —script=mysql-info.nse –sV –sC 192.168.0.9
https://st-lab.tistory.com/100
nse파일
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# ls | grep http http-adobe-coldfusion-apsa1301.nse http-affiliate-id.nse http-apache-negotiation.nse http-apache-server-status.nse http-aspnet-debug.nse http-auth-finder.nse http-auth.nse http-avaya-ipoffice-users.nse http-awstatstotals-exec.nse http-axis2-dir-traversal.nse http-backup-finder.nse http-barracuda-dir-traversal.nse http-bigip-cookie.nse http-brute.nse http-cakephp-version.nse http-chrono.nse http-cisco-anyconnect.nse http-coldfusion-subzero.nse http-comments-displayer.nse http-config-backup.nse http-cookie-flags.nse http-cors.nse http-cross-domain-policy.nse http-csrf.nse http-date.nse http-default-accounts.nse http-devframework.nse http-dlink-backdoor.nse http-dombased-xss.nse http-domino-enum-passwords.nse http-drupal-enum-users.nse http-drupal-enum.nse http-enum.nse http-errors.nse http-exif-spider.nse http-favicon.nse http-feed.nse http-fetch.nse http-fileupload-exploiter.nse http-form-brute.nse http-form-fuzzer.nse http-frontpage-login.nse http-generator.nse http-git.nse http-gitweb-projects-enum.nse http-google-malware.nse http-grep.nse http-headers.nse http-hp-ilo-info.nse http-huawei-hg5xx-vuln.nse http-icloud-findmyiphone.nse http-icloud-sendmsg.nse http-iis-short-name-brute.nse http-iis-webdav-vuln.nse http-internal-ip-disclosure.nse http-joomla-brute.nse http-jsonp-detection.nse http-litespeed-sourcecode-download.nse http-ls.nse http-majordomo2-dir-traversal.nse http-malware-host.nse http-mcmp.nse http-method-tamper.nse http-methods.nse http-mobileversion-checker.nse http-ntlm-info.nse http-open-proxy.nse http-open-redirect.nse http-passwd.nse http-php-version.nse http-phpmyadmin-dir-traversal.nse http-phpself-xss.nse http-proxy-brute.nse http-put.nse http-qnap-nas-info.nse http-referer-checker.nse http-rfi-spider.nse http-robots.txt.nse http-robtex-reverse-ip.nse http-robtex-shared-ns.nse http-sap-netweaver-leak.nse http-security-headers.nse http-server-header.nse http-shellshock.nse http-sitemap-generator.nse http-slowloris-check.nse http-slowloris.nse http-sql-injection.nse http-stored-xss.nse http-svn-enum.nse http-svn-info.nse http-title.nse http-tplink-dir-traversal.nse http-trace.nse http-traceroute.nse http-trane-info.nse http-unsafe-output-escaping.nse http-useragent-tester.nse http-userdir-enum.nse http-vhosts.nse http-virustotal.nse http-vlcstreamer-ls.nse http-vmware-path-vuln.nse http-vuln-cve2006-3392.nse http-vuln-cve2009-3960.nse http-vuln-cve2010-0738.nse http-vuln-cve2010-2861.nse http-vuln-cve2011-3192.nse http-vuln-cve2011-3368.nse http-vuln-cve2012-1823.nse http-vuln-cve2013-0156.nse http-vuln-cve2013-6786.nse http-vuln-cve2013-7091.nse http-vuln-cve2014-2126.nse http-vuln-cve2014-2127.nse http-vuln-cve2014-2128.nse http-vuln-cve2014-2129.nse http-vuln-cve2014-3704.nse http-vuln-cve2014-8877.nse http-vuln-cve2015-1427.nse http-vuln-cve2015-1635.nse http-vuln-cve2017-1001000.nse http-vuln-cve2017-5638.nse http-vuln-cve2017-5689.nse http-vuln-cve2017-8917.nse http-vuln-misfortune-cookie.nse http-vuln-wnr1000-creds.nse http-waf-detect.nse http-waf-fingerprint.nse http-webdav-scan.nse http-wordpress-brute.nse http-wordpress-enum.nse http-wordpress-users.nse http-xssed.nse https-redirect.nse ip-https-discover.nse membase-http-info.nse riak-http-info.nse ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# |
http 관련 스크립트를 전부 실행
nmap –p 80 –sV —script “http-*” 192.168.0.9
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# ls | grep "http-" http-adobe-coldfusion-apsa1301.nse http-affiliate-id.nse http-apache-negotiation.nse http-apache-server-status.nse http-aspnet-debug.nse http-auth-finder.nse http-auth.nse http-avaya-ipoffice-users.nse http-awstatstotals-exec.nse http-axis2-dir-traversal.nse http-backup-finder.nse http-barracuda-dir-traversal.nse http-bigip-cookie.nse http-brute.nse http-cakephp-version.nse http-chrono.nse http-cisco-anyconnect.nse http-coldfusion-subzero.nse http-comments-displayer.nse http-config-backup.nse http-cookie-flags.nse http-cors.nse http-cross-domain-policy.nse http-csrf.nse http-date.nse http-default-accounts.nse http-devframework.nse http-dlink-backdoor.nse http-dombased-xss.nse http-domino-enum-passwords.nse http-drupal-enum-users.nse http-drupal-enum.nse http-enum.nse http-errors.nse http-exif-spider.nse http-favicon.nse http-feed.nse http-fetch.nse http-fileupload-exploiter.nse http-form-brute.nse http-form-fuzzer.nse http-frontpage-login.nse http-generator.nse http-git.nse http-gitweb-projects-enum.nse http-google-malware.nse http-grep.nse http-headers.nse http-hp-ilo-info.nse http-huawei-hg5xx-vuln.nse http-icloud-findmyiphone.nse http-icloud-sendmsg.nse http-iis-short-name-brute.nse http-iis-webdav-vuln.nse http-internal-ip-disclosure.nse http-joomla-brute.nse http-jsonp-detection.nse http-litespeed-sourcecode-download.nse http-ls.nse http-majordomo2-dir-traversal.nse http-malware-host.nse http-mcmp.nse http-method-tamper.nse http-methods.nse http-mobileversion-checker.nse http-ntlm-info.nse http-open-proxy.nse http-open-redirect.nse http-passwd.nse http-php-version.nse http-phpmyadmin-dir-traversal.nse http-phpself-xss.nse http-proxy-brute.nse http-put.nse http-qnap-nas-info.nse http-referer-checker.nse http-rfi-spider.nse http-robots.txt.nse http-robtex-reverse-ip.nse http-robtex-shared-ns.nse http-sap-netweaver-leak.nse http-security-headers.nse http-server-header.nse http-shellshock.nse http-sitemap-generator.nse http-slowloris-check.nse http-slowloris.nse http-sql-injection.nse http-stored-xss.nse http-svn-enum.nse http-svn-info.nse http-title.nse http-tplink-dir-traversal.nse http-trace.nse http-traceroute.nse http-trane-info.nse http-unsafe-output-escaping.nse http-useragent-tester.nse http-userdir-enum.nse http-vhosts.nse http-virustotal.nse http-vlcstreamer-ls.nse http-vmware-path-vuln.nse http-vuln-cve2006-3392.nse http-vuln-cve2009-3960.nse http-vuln-cve2010-0738.nse http-vuln-cve2010-2861.nse http-vuln-cve2011-3192.nse http-vuln-cve2011-3368.nse http-vuln-cve2012-1823.nse http-vuln-cve2013-0156.nse http-vuln-cve2013-6786.nse http-vuln-cve2013-7091.nse http-vuln-cve2014-2126.nse http-vuln-cve2014-2127.nse http-vuln-cve2014-2128.nse http-vuln-cve2014-2129.nse http-vuln-cve2014-3704.nse http-vuln-cve2014-8877.nse http-vuln-cve2015-1427.nse http-vuln-cve2015-1635.nse http-vuln-cve2017-1001000.nse http-vuln-cve2017-5638.nse http-vuln-cve2017-5689.nse http-vuln-cve2017-8917.nse http-vuln-misfortune-cookie.nse http-vuln-wnr1000-creds.nse http-waf-detect.nse http-waf-fingerprint.nse http-webdav-scan.nse http-wordpress-brute.nse http-wordpress-enum.nse http-wordpress-users.nse http-xssed.nse membase-http-info.nse riak-http-info.nse ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# |
NMAP ---> 스캐너 : 네트워크 Discovery ---> Host ---> port scan
NMAP + 추가 모듈 (확장기능)
NSE 분류
Network discovery
More Sophisticated and accurate OS version detction
기본 NMAP과 비교하여 정밀한 탐지가 가능하다.
3. Vulnerability Detection
4. Backdoor Detection
5. Vulnerability Exploitation ---> #취약점 공격해서 침투테스트까지 가능하다.
NMAP + Script : 정교하거나 추가된 기능을 사용할 수 있다.
Script ---> NMAP에서 사용하는 script의 확장자 : nse
현재 설치된 운영체제에서 nse 파일을 찾아보자.
find / -name *.nse #파일을 찾음.
locate *.nse #파일의 위치를 찾아준다.
nse 스크립트 파일의 위치 : /usr/share/nmap/scripts/
nmap의 스크립트 파일은 업데이트가 가능하다.
nmap --script-update
nmap --script-updatedb
dns-brute.nse ===> 딕셔너리 어택 : 대상 : DNS #루비 코드로 작성되어 있다.
--->dns enum 공격
사용법 : 기본 NMAP
nmap –p 53 —script dns-brute.nse [공격대상 dns서버]
#툴마다 기능이 다르기 때문에 다양하게 사용하고 비교하자.
www.ubiedu.co.kr / 14.36.28.250
--> 버츄얼 호스팅이 되어 있다.
--> 도메인 주소는 https 보안이 되어 있다.
--> IP로 접속 하였을때는 보안이 취약할 수도 있다.
대상 사이트가 웹 서버일 때
http 페이지를 식별한다.
http-enum.nse
nmap —script http-enum.nse 192.168.0.9
스캔 완료 화면
스캐너 : vulscan.nse #취약점 탐색
기본 NSE에는 없음 --> 추가 다운로드 필요
cd /usr/share/nmap/scripts/
mkdir addon
cd addon
wget https://github.com/vulnersCom/nmap-vulners/archive/refs/heads/master.zip
unzip master.zip
nmap-vulners-master/vulners.nse 획득
https://podman.io/ : pod를 적게 사용하는 경우
kubernetes ---> 이름이 갈다. ---> k9s ---> : 구버네티스 오케이스트레이션 프로그램 자체가 무겁다.
-ubernete
==> micro Kuvernetes
--> k9s
웹서버 취약점 분석 (CVE 취약점 분석)
nmap –sV –p 80 —script=nmap-vulners-master/vulners.nse
msfconsole과 연계 가능 #CVE코드 검색
msfconsole
search [CVE코드]
ls | grep ssh
ssh-brute.nse : ssh 서비스에 대한 브루트포스를 진행
필수조건 : user.lst
pw.lst
기본으로 만들어 쓰자.
echo “aaa
bbb
ccc“ > user.lst
echo “aaa
bbb
ccc“ > pw.lst
공격코드
nmap -n -p22 --script ssh-brute.nse --script-args userdb=user.lst,passdb=pw.lst 192.168.0.9
부르트포스 날림
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# nmap -n -p22 --script ssh-brute.nse --script-args userdb=user.lst,passdb=pw.lst 192.168.0.9 Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-30 10:42 KST NSE: [ssh-brute] Trying username/password pair: aaa:aaa NSE: [ssh-brute] Trying username/password pair: bbb:bbb NSE: [ssh-brute] Trying username/password pair: ccc:ccc NSE: [ssh-brute] Trying username/password pair: bbb:aaa NSE: [ssh-brute] Trying username/password pair: ccc:aaa NSE: [ssh-brute] Trying username/password pair: aaa:bbb NSE: [ssh-brute] Trying username/password pair: ccc:bbb NSE: [ssh-brute] Trying username/password pair: aaa:ccc NSE: [ssh-brute] Trying username/password pair: bbb:ccc Nmap scan report for 192.168.0.9 Host is up (0.00024s latency). |
SMB 유저 탐색
smb-enum.nse
nmap –n –p139,445 --script=smb-enum-users --script-args=smbuername=“test”, \smbpassword=“asd123!@”,samronly 192.168.0.9
firewalk.nse (방화벽에 적용된 룰 확인) +@
대상 서버에 설정되어 있는 방화벽 설정값을 확인 ---> port scan
추가 기능 --> traceroute : 경로 확인
nmap --script firewalk.nse --traceroute 192.168.0.9
myspl-info.nse
mysql정보와 버전 상태 // --> password salt : 소금(salt) ---> 패스워드를 알아내기 위한 키 (패스워드)
nmap —script=mysql-info.nse –sV –sC 192.168.0.9
https://st-lab.tistory.com/100
nse파일
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# ls | grep http http-adobe-coldfusion-apsa1301.nse http-affiliate-id.nse http-apache-negotiation.nse http-apache-server-status.nse http-aspnet-debug.nse http-auth-finder.nse http-auth.nse http-avaya-ipoffice-users.nse http-awstatstotals-exec.nse http-axis2-dir-traversal.nse http-backup-finder.nse http-barracuda-dir-traversal.nse http-bigip-cookie.nse http-brute.nse http-cakephp-version.nse http-chrono.nse http-cisco-anyconnect.nse http-coldfusion-subzero.nse http-comments-displayer.nse http-config-backup.nse http-cookie-flags.nse http-cors.nse http-cross-domain-policy.nse http-csrf.nse http-date.nse http-default-accounts.nse http-devframework.nse http-dlink-backdoor.nse http-dombased-xss.nse http-domino-enum-passwords.nse http-drupal-enum-users.nse http-drupal-enum.nse http-enum.nse http-errors.nse http-exif-spider.nse http-favicon.nse http-feed.nse http-fetch.nse http-fileupload-exploiter.nse http-form-brute.nse http-form-fuzzer.nse http-frontpage-login.nse http-generator.nse http-git.nse http-gitweb-projects-enum.nse http-google-malware.nse http-grep.nse http-headers.nse http-hp-ilo-info.nse http-huawei-hg5xx-vuln.nse http-icloud-findmyiphone.nse http-icloud-sendmsg.nse http-iis-short-name-brute.nse http-iis-webdav-vuln.nse http-internal-ip-disclosure.nse http-joomla-brute.nse http-jsonp-detection.nse http-litespeed-sourcecode-download.nse http-ls.nse http-majordomo2-dir-traversal.nse http-malware-host.nse http-mcmp.nse http-method-tamper.nse http-methods.nse http-mobileversion-checker.nse http-ntlm-info.nse http-open-proxy.nse http-open-redirect.nse http-passwd.nse http-php-version.nse http-phpmyadmin-dir-traversal.nse http-phpself-xss.nse http-proxy-brute.nse http-put.nse http-qnap-nas-info.nse http-referer-checker.nse http-rfi-spider.nse http-robots.txt.nse http-robtex-reverse-ip.nse http-robtex-shared-ns.nse http-sap-netweaver-leak.nse http-security-headers.nse http-server-header.nse http-shellshock.nse http-sitemap-generator.nse http-slowloris-check.nse http-slowloris.nse http-sql-injection.nse http-stored-xss.nse http-svn-enum.nse http-svn-info.nse http-title.nse http-tplink-dir-traversal.nse http-trace.nse http-traceroute.nse http-trane-info.nse http-unsafe-output-escaping.nse http-useragent-tester.nse http-userdir-enum.nse http-vhosts.nse http-virustotal.nse http-vlcstreamer-ls.nse http-vmware-path-vuln.nse http-vuln-cve2006-3392.nse http-vuln-cve2009-3960.nse http-vuln-cve2010-0738.nse http-vuln-cve2010-2861.nse http-vuln-cve2011-3192.nse http-vuln-cve2011-3368.nse http-vuln-cve2012-1823.nse http-vuln-cve2013-0156.nse http-vuln-cve2013-6786.nse http-vuln-cve2013-7091.nse http-vuln-cve2014-2126.nse http-vuln-cve2014-2127.nse http-vuln-cve2014-2128.nse http-vuln-cve2014-2129.nse http-vuln-cve2014-3704.nse http-vuln-cve2014-8877.nse http-vuln-cve2015-1427.nse http-vuln-cve2015-1635.nse http-vuln-cve2017-1001000.nse http-vuln-cve2017-5638.nse http-vuln-cve2017-5689.nse http-vuln-cve2017-8917.nse http-vuln-misfortune-cookie.nse http-vuln-wnr1000-creds.nse http-waf-detect.nse http-waf-fingerprint.nse http-webdav-scan.nse http-wordpress-brute.nse http-wordpress-enum.nse http-wordpress-users.nse http-xssed.nse https-redirect.nse ip-https-discover.nse membase-http-info.nse riak-http-info.nse ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# |
http 관련 스크립트를 전부 실행
nmap –p 80 –sV —script “http-*” 192.168.0.9
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# ls | grep "http-" http-adobe-coldfusion-apsa1301.nse http-affiliate-id.nse http-apache-negotiation.nse http-apache-server-status.nse http-aspnet-debug.nse http-auth-finder.nse http-auth.nse http-avaya-ipoffice-users.nse http-awstatstotals-exec.nse http-axis2-dir-traversal.nse http-backup-finder.nse http-barracuda-dir-traversal.nse http-bigip-cookie.nse http-brute.nse http-cakephp-version.nse http-chrono.nse http-cisco-anyconnect.nse http-coldfusion-subzero.nse http-comments-displayer.nse http-config-backup.nse http-cookie-flags.nse http-cors.nse http-cross-domain-policy.nse http-csrf.nse http-date.nse http-default-accounts.nse http-devframework.nse http-dlink-backdoor.nse http-dombased-xss.nse http-domino-enum-passwords.nse http-drupal-enum-users.nse http-drupal-enum.nse http-enum.nse http-errors.nse http-exif-spider.nse http-favicon.nse http-feed.nse http-fetch.nse http-fileupload-exploiter.nse http-form-brute.nse http-form-fuzzer.nse http-frontpage-login.nse http-generator.nse http-git.nse http-gitweb-projects-enum.nse http-google-malware.nse http-grep.nse http-headers.nse http-hp-ilo-info.nse http-huawei-hg5xx-vuln.nse http-icloud-findmyiphone.nse http-icloud-sendmsg.nse http-iis-short-name-brute.nse http-iis-webdav-vuln.nse http-internal-ip-disclosure.nse http-joomla-brute.nse http-jsonp-detection.nse http-litespeed-sourcecode-download.nse http-ls.nse http-majordomo2-dir-traversal.nse http-malware-host.nse http-mcmp.nse http-method-tamper.nse http-methods.nse http-mobileversion-checker.nse http-ntlm-info.nse http-open-proxy.nse http-open-redirect.nse http-passwd.nse http-php-version.nse http-phpmyadmin-dir-traversal.nse http-phpself-xss.nse http-proxy-brute.nse http-put.nse http-qnap-nas-info.nse http-referer-checker.nse http-rfi-spider.nse http-robots.txt.nse http-robtex-reverse-ip.nse http-robtex-shared-ns.nse http-sap-netweaver-leak.nse http-security-headers.nse http-server-header.nse http-shellshock.nse http-sitemap-generator.nse http-slowloris-check.nse http-slowloris.nse http-sql-injection.nse http-stored-xss.nse http-svn-enum.nse http-svn-info.nse http-title.nse http-tplink-dir-traversal.nse http-trace.nse http-traceroute.nse http-trane-info.nse http-unsafe-output-escaping.nse http-useragent-tester.nse http-userdir-enum.nse http-vhosts.nse http-virustotal.nse http-vlcstreamer-ls.nse http-vmware-path-vuln.nse http-vuln-cve2006-3392.nse http-vuln-cve2009-3960.nse http-vuln-cve2010-0738.nse http-vuln-cve2010-2861.nse http-vuln-cve2011-3192.nse http-vuln-cve2011-3368.nse http-vuln-cve2012-1823.nse http-vuln-cve2013-0156.nse http-vuln-cve2013-6786.nse http-vuln-cve2013-7091.nse http-vuln-cve2014-2126.nse http-vuln-cve2014-2127.nse http-vuln-cve2014-2128.nse http-vuln-cve2014-2129.nse http-vuln-cve2014-3704.nse http-vuln-cve2014-8877.nse http-vuln-cve2015-1427.nse http-vuln-cve2015-1635.nse http-vuln-cve2017-1001000.nse http-vuln-cve2017-5638.nse http-vuln-cve2017-5689.nse http-vuln-cve2017-8917.nse http-vuln-misfortune-cookie.nse http-vuln-wnr1000-creds.nse http-waf-detect.nse http-waf-fingerprint.nse http-webdav-scan.nse http-wordpress-brute.nse http-wordpress-enum.nse http-wordpress-users.nse http-xssed.nse membase-http-info.nse riak-http-info.nse ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# |
NMAP + 추가 모듈 (확장기능)
NSE 분류
Network discovery
More Sophisticated and accurate OS version detction
기본 NMAP과 비교하여 정밀한 탐지가 가능하다.
3. Vulnerability Detection
4. Backdoor Detection
5. Vulnerability Exploitation ---> #취약점 공격해서 침투테스트까지 가능하다.
NMAP + Script : 정교하거나 추가된 기능을 사용할 수 있다.
Script ---> NMAP에서 사용하는 script의 확장자 : nse
현재 설치된 운영체제에서 nse 파일을 찾아보자.
find / -name *.nse #파일을 찾음.
locate *.nse #파일의 위치를 찾아준다.
nse 스크립트 파일의 위치 : /usr/share/nmap/scripts/
nmap의 스크립트 파일은 업데이트가 가능하다.
nmap --script-update
nmap --script-updatedb
dns-brute.nse ===> 딕셔너리 어택 : 대상 : DNS #루비 코드로 작성되어 있다.
--->dns enum 공격
사용법 : 기본 NMAP
nmap –p 53 —script dns-brute.nse [공격대상 dns서버]
#툴마다 기능이 다르기 때문에 다양하게 사용하고 비교하자.
www.ubiedu.co.kr / 14.36.28.250
--> 버츄얼 호스팅이 되어 있다.
--> 도메인 주소는 https 보안이 되어 있다.
--> IP로 접속 하였을때는 보안이 취약할 수도 있다.
대상 사이트가 웹 서버일 때
http 페이지를 식별한다.
http-enum.nse
nmap —script http-enum.nse 192.168.0.9
스캔 완료 화면
스캐너 : vulscan.nse #취약점 탐색
기본 NSE에는 없음 --> 추가 다운로드 필요
cd /usr/share/nmap/scripts/
mkdir addon
cd addon
wget https://github.com/vulnersCom/nmap-vulners/archive/refs/heads/master.zip
unzip master.zip
nmap-vulners-master/vulners.nse 획득
https://podman.io/ : pod를 적게 사용하는 경우
kubernetes ---> 이름이 갈다. ---> k9s ---> : 구버네티스 오케이스트레이션 프로그램 자체가 무겁다.
-ubernete
==> micro Kuvernetes
--> k9s
웹서버 취약점 분석 (CVE 취약점 분석)
nmap –sV –p 80 —script=nmap-vulners-master/vulners.nse
msfconsole과 연계 가능 #CVE코드 검색
msfconsole
search [CVE코드]
ls | grep ssh
ssh-brute.nse : ssh 서비스에 대한 브루트포스를 진행
필수조건 : user.lst
pw.lst
기본으로 만들어 쓰자.
echo “aaa
bbb
ccc“ > user.lst
echo “aaa
bbb
ccc“ > pw.lst
공격코드
nmap -n -p22 --script ssh-brute.nse --script-args userdb=user.lst,passdb=pw.lst 192.168.0.9
부르트포스 날림
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# nmap -n -p22 --script ssh-brute.nse --script-args userdb=user.lst,passdb=pw.lst 192.168.0.9 Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-30 10:42 KST NSE: [ssh-brute] Trying username/password pair: aaa:aaa NSE: [ssh-brute] Trying username/password pair: bbb:bbb NSE: [ssh-brute] Trying username/password pair: ccc:ccc NSE: [ssh-brute] Trying username/password pair: bbb:aaa NSE: [ssh-brute] Trying username/password pair: ccc:aaa NSE: [ssh-brute] Trying username/password pair: aaa:bbb NSE: [ssh-brute] Trying username/password pair: ccc:bbb NSE: [ssh-brute] Trying username/password pair: aaa:ccc NSE: [ssh-brute] Trying username/password pair: bbb:ccc Nmap scan report for 192.168.0.9 Host is up (0.00024s latency). |
SMB 유저 탐색
smb-enum.nse
nmap –n –p139,445 --script=smb-enum-users --script-args=smbuername=“test”, \smbpassword=“asd123!@”,samronly 192.168.0.9
firewalk.nse (방화벽에 적용된 룰 확인) +@
대상 서버에 설정되어 있는 방화벽 설정값을 확인 ---> port scan
추가 기능 --> traceroute : 경로 확인
nmap --script firewalk.nse --traceroute 192.168.0.9
myspl-info.nse
mysql정보와 버전 상태 // --> password salt : 소금(salt) ---> 패스워드를 알아내기 위한 키 (패스워드)
nmap —script=mysql-info.nse –sV –sC 192.168.0.9
https://st-lab.tistory.com/100
nse파일
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# ls | grep http http-adobe-coldfusion-apsa1301.nse http-affiliate-id.nse http-apache-negotiation.nse http-apache-server-status.nse http-aspnet-debug.nse http-auth-finder.nse http-auth.nse http-avaya-ipoffice-users.nse http-awstatstotals-exec.nse http-axis2-dir-traversal.nse http-backup-finder.nse http-barracuda-dir-traversal.nse http-bigip-cookie.nse http-brute.nse http-cakephp-version.nse http-chrono.nse http-cisco-anyconnect.nse http-coldfusion-subzero.nse http-comments-displayer.nse http-config-backup.nse http-cookie-flags.nse http-cors.nse http-cross-domain-policy.nse http-csrf.nse http-date.nse http-default-accounts.nse http-devframework.nse http-dlink-backdoor.nse http-dombased-xss.nse http-domino-enum-passwords.nse http-drupal-enum-users.nse http-drupal-enum.nse http-enum.nse http-errors.nse http-exif-spider.nse http-favicon.nse http-feed.nse http-fetch.nse http-fileupload-exploiter.nse http-form-brute.nse http-form-fuzzer.nse http-frontpage-login.nse http-generator.nse http-git.nse http-gitweb-projects-enum.nse http-google-malware.nse http-grep.nse http-headers.nse http-hp-ilo-info.nse http-huawei-hg5xx-vuln.nse http-icloud-findmyiphone.nse http-icloud-sendmsg.nse http-iis-short-name-brute.nse http-iis-webdav-vuln.nse http-internal-ip-disclosure.nse http-joomla-brute.nse http-jsonp-detection.nse http-litespeed-sourcecode-download.nse http-ls.nse http-majordomo2-dir-traversal.nse http-malware-host.nse http-mcmp.nse http-method-tamper.nse http-methods.nse http-mobileversion-checker.nse http-ntlm-info.nse http-open-proxy.nse http-open-redirect.nse http-passwd.nse http-php-version.nse http-phpmyadmin-dir-traversal.nse http-phpself-xss.nse http-proxy-brute.nse http-put.nse http-qnap-nas-info.nse http-referer-checker.nse http-rfi-spider.nse http-robots.txt.nse http-robtex-reverse-ip.nse http-robtex-shared-ns.nse http-sap-netweaver-leak.nse http-security-headers.nse http-server-header.nse http-shellshock.nse http-sitemap-generator.nse http-slowloris-check.nse http-slowloris.nse http-sql-injection.nse http-stored-xss.nse http-svn-enum.nse http-svn-info.nse http-title.nse http-tplink-dir-traversal.nse http-trace.nse http-traceroute.nse http-trane-info.nse http-unsafe-output-escaping.nse http-useragent-tester.nse http-userdir-enum.nse http-vhosts.nse http-virustotal.nse http-vlcstreamer-ls.nse http-vmware-path-vuln.nse http-vuln-cve2006-3392.nse http-vuln-cve2009-3960.nse http-vuln-cve2010-0738.nse http-vuln-cve2010-2861.nse http-vuln-cve2011-3192.nse http-vuln-cve2011-3368.nse http-vuln-cve2012-1823.nse http-vuln-cve2013-0156.nse http-vuln-cve2013-6786.nse http-vuln-cve2013-7091.nse http-vuln-cve2014-2126.nse http-vuln-cve2014-2127.nse http-vuln-cve2014-2128.nse http-vuln-cve2014-2129.nse http-vuln-cve2014-3704.nse http-vuln-cve2014-8877.nse http-vuln-cve2015-1427.nse http-vuln-cve2015-1635.nse http-vuln-cve2017-1001000.nse http-vuln-cve2017-5638.nse http-vuln-cve2017-5689.nse http-vuln-cve2017-8917.nse http-vuln-misfortune-cookie.nse http-vuln-wnr1000-creds.nse http-waf-detect.nse http-waf-fingerprint.nse http-webdav-scan.nse http-wordpress-brute.nse http-wordpress-enum.nse http-wordpress-users.nse http-xssed.nse https-redirect.nse ip-https-discover.nse membase-http-info.nse riak-http-info.nse ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# |
http 관련 스크립트를 전부 실행
nmap –p 80 –sV —script “http-*” 192.168.0.9
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# ls | grep "http-" http-adobe-coldfusion-apsa1301.nse http-affiliate-id.nse http-apache-negotiation.nse http-apache-server-status.nse http-aspnet-debug.nse http-auth-finder.nse http-auth.nse http-avaya-ipoffice-users.nse http-awstatstotals-exec.nse http-axis2-dir-traversal.nse http-backup-finder.nse http-barracuda-dir-traversal.nse http-bigip-cookie.nse http-brute.nse http-cakephp-version.nse http-chrono.nse http-cisco-anyconnect.nse http-coldfusion-subzero.nse http-comments-displayer.nse http-config-backup.nse http-cookie-flags.nse http-cors.nse http-cross-domain-policy.nse http-csrf.nse http-date.nse http-default-accounts.nse http-devframework.nse http-dlink-backdoor.nse http-dombased-xss.nse http-domino-enum-passwords.nse http-drupal-enum-users.nse http-drupal-enum.nse http-enum.nse http-errors.nse http-exif-spider.nse http-favicon.nse http-feed.nse http-fetch.nse http-fileupload-exploiter.nse http-form-brute.nse http-form-fuzzer.nse http-frontpage-login.nse http-generator.nse http-git.nse http-gitweb-projects-enum.nse http-google-malware.nse http-grep.nse http-headers.nse http-hp-ilo-info.nse http-huawei-hg5xx-vuln.nse http-icloud-findmyiphone.nse http-icloud-sendmsg.nse http-iis-short-name-brute.nse http-iis-webdav-vuln.nse http-internal-ip-disclosure.nse http-joomla-brute.nse http-jsonp-detection.nse http-litespeed-sourcecode-download.nse http-ls.nse http-majordomo2-dir-traversal.nse http-malware-host.nse http-mcmp.nse http-method-tamper.nse http-methods.nse http-mobileversion-checker.nse http-ntlm-info.nse http-open-proxy.nse http-open-redirect.nse http-passwd.nse http-php-version.nse http-phpmyadmin-dir-traversal.nse http-phpself-xss.nse http-proxy-brute.nse http-put.nse http-qnap-nas-info.nse http-referer-checker.nse http-rfi-spider.nse http-robots.txt.nse http-robtex-reverse-ip.nse http-robtex-shared-ns.nse http-sap-netweaver-leak.nse http-security-headers.nse http-server-header.nse http-shellshock.nse http-sitemap-generator.nse http-slowloris-check.nse http-slowloris.nse http-sql-injection.nse http-stored-xss.nse http-svn-enum.nse http-svn-info.nse http-title.nse http-tplink-dir-traversal.nse http-trace.nse http-traceroute.nse http-trane-info.nse http-unsafe-output-escaping.nse http-useragent-tester.nse http-userdir-enum.nse http-vhosts.nse http-virustotal.nse http-vlcstreamer-ls.nse http-vmware-path-vuln.nse http-vuln-cve2006-3392.nse http-vuln-cve2009-3960.nse http-vuln-cve2010-0738.nse http-vuln-cve2010-2861.nse http-vuln-cve2011-3192.nse http-vuln-cve2011-3368.nse http-vuln-cve2012-1823.nse http-vuln-cve2013-0156.nse http-vuln-cve2013-6786.nse http-vuln-cve2013-7091.nse http-vuln-cve2014-2126.nse http-vuln-cve2014-2127.nse http-vuln-cve2014-2128.nse http-vuln-cve2014-2129.nse http-vuln-cve2014-3704.nse http-vuln-cve2014-8877.nse http-vuln-cve2015-1427.nse http-vuln-cve2015-1635.nse http-vuln-cve2017-1001000.nse http-vuln-cve2017-5638.nse http-vuln-cve2017-5689.nse http-vuln-cve2017-8917.nse http-vuln-misfortune-cookie.nse http-vuln-wnr1000-creds.nse http-waf-detect.nse http-waf-fingerprint.nse http-webdav-scan.nse http-wordpress-brute.nse http-wordpress-enum.nse http-wordpress-users.nse http-xssed.nse membase-http-info.nse riak-http-info.nse ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# |
NSE 분류
Network discovery
More Sophisticated and accurate OS version detction
기본 NMAP과 비교하여 정밀한 탐지가 가능하다.
3. Vulnerability Detection
4. Backdoor Detection
5. Vulnerability Exploitation ---> #취약점 공격해서 침투테스트까지 가능하다.
NMAP + Script : 정교하거나 추가된 기능을 사용할 수 있다.
Script ---> NMAP에서 사용하는 script의 확장자 : nse
현재 설치된 운영체제에서 nse 파일을 찾아보자.
find / -name *.nse #파일을 찾음.
locate *.nse #파일의 위치를 찾아준다.
nse 스크립트 파일의 위치 : /usr/share/nmap/scripts/
nmap의 스크립트 파일은 업데이트가 가능하다.
nmap --script-update
nmap --script-updatedb
dns-brute.nse ===> 딕셔너리 어택 : 대상 : DNS #루비 코드로 작성되어 있다.
--->dns enum 공격
사용법 : 기본 NMAP
nmap –p 53 —script dns-brute.nse [공격대상 dns서버]
#툴마다 기능이 다르기 때문에 다양하게 사용하고 비교하자.
www.ubiedu.co.kr / 14.36.28.250
--> 버츄얼 호스팅이 되어 있다.
--> 도메인 주소는 https 보안이 되어 있다.
--> IP로 접속 하였을때는 보안이 취약할 수도 있다.
대상 사이트가 웹 서버일 때
http 페이지를 식별한다.
http-enum.nse
nmap —script http-enum.nse 192.168.0.9
스캔 완료 화면
스캐너 : vulscan.nse #취약점 탐색
기본 NSE에는 없음 --> 추가 다운로드 필요
cd /usr/share/nmap/scripts/
mkdir addon
cd addon
wget https://github.com/vulnersCom/nmap-vulners/archive/refs/heads/master.zip
unzip master.zip
nmap-vulners-master/vulners.nse 획득
https://podman.io/ : pod를 적게 사용하는 경우
kubernetes ---> 이름이 갈다. ---> k9s ---> : 구버네티스 오케이스트레이션 프로그램 자체가 무겁다.
-ubernete
==> micro Kuvernetes
--> k9s
웹서버 취약점 분석 (CVE 취약점 분석)
nmap –sV –p 80 —script=nmap-vulners-master/vulners.nse
msfconsole과 연계 가능 #CVE코드 검색
msfconsole
search [CVE코드]
ls | grep ssh
ssh-brute.nse : ssh 서비스에 대한 브루트포스를 진행
필수조건 : user.lst
pw.lst
기본으로 만들어 쓰자.
echo “aaa
bbb
ccc“ > user.lst
echo “aaa
bbb
ccc“ > pw.lst
공격코드
nmap -n -p22 --script ssh-brute.nse --script-args userdb=user.lst,passdb=pw.lst 192.168.0.9
부르트포스 날림
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# nmap -n -p22 --script ssh-brute.nse --script-args userdb=user.lst,passdb=pw.lst 192.168.0.9 Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-30 10:42 KST NSE: [ssh-brute] Trying username/password pair: aaa:aaa NSE: [ssh-brute] Trying username/password pair: bbb:bbb NSE: [ssh-brute] Trying username/password pair: ccc:ccc NSE: [ssh-brute] Trying username/password pair: bbb:aaa NSE: [ssh-brute] Trying username/password pair: ccc:aaa NSE: [ssh-brute] Trying username/password pair: aaa:bbb NSE: [ssh-brute] Trying username/password pair: ccc:bbb NSE: [ssh-brute] Trying username/password pair: aaa:ccc NSE: [ssh-brute] Trying username/password pair: bbb:ccc Nmap scan report for 192.168.0.9 Host is up (0.00024s latency). |
SMB 유저 탐색
smb-enum.nse
nmap –n –p139,445 --script=smb-enum-users --script-args=smbuername=“test”, \smbpassword=“asd123!@”,samronly 192.168.0.9
firewalk.nse (방화벽에 적용된 룰 확인) +@
대상 서버에 설정되어 있는 방화벽 설정값을 확인 ---> port scan
추가 기능 --> traceroute : 경로 확인
nmap --script firewalk.nse --traceroute 192.168.0.9
myspl-info.nse
mysql정보와 버전 상태 // --> password salt : 소금(salt) ---> 패스워드를 알아내기 위한 키 (패스워드)
nmap —script=mysql-info.nse –sV –sC 192.168.0.9
https://st-lab.tistory.com/100
nse파일
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# ls | grep http http-adobe-coldfusion-apsa1301.nse http-affiliate-id.nse http-apache-negotiation.nse http-apache-server-status.nse http-aspnet-debug.nse http-auth-finder.nse http-auth.nse http-avaya-ipoffice-users.nse http-awstatstotals-exec.nse http-axis2-dir-traversal.nse http-backup-finder.nse http-barracuda-dir-traversal.nse http-bigip-cookie.nse http-brute.nse http-cakephp-version.nse http-chrono.nse http-cisco-anyconnect.nse http-coldfusion-subzero.nse http-comments-displayer.nse http-config-backup.nse http-cookie-flags.nse http-cors.nse http-cross-domain-policy.nse http-csrf.nse http-date.nse http-default-accounts.nse http-devframework.nse http-dlink-backdoor.nse http-dombased-xss.nse http-domino-enum-passwords.nse http-drupal-enum-users.nse http-drupal-enum.nse http-enum.nse http-errors.nse http-exif-spider.nse http-favicon.nse http-feed.nse http-fetch.nse http-fileupload-exploiter.nse http-form-brute.nse http-form-fuzzer.nse http-frontpage-login.nse http-generator.nse http-git.nse http-gitweb-projects-enum.nse http-google-malware.nse http-grep.nse http-headers.nse http-hp-ilo-info.nse http-huawei-hg5xx-vuln.nse http-icloud-findmyiphone.nse http-icloud-sendmsg.nse http-iis-short-name-brute.nse http-iis-webdav-vuln.nse http-internal-ip-disclosure.nse http-joomla-brute.nse http-jsonp-detection.nse http-litespeed-sourcecode-download.nse http-ls.nse http-majordomo2-dir-traversal.nse http-malware-host.nse http-mcmp.nse http-method-tamper.nse http-methods.nse http-mobileversion-checker.nse http-ntlm-info.nse http-open-proxy.nse http-open-redirect.nse http-passwd.nse http-php-version.nse http-phpmyadmin-dir-traversal.nse http-phpself-xss.nse http-proxy-brute.nse http-put.nse http-qnap-nas-info.nse http-referer-checker.nse http-rfi-spider.nse http-robots.txt.nse http-robtex-reverse-ip.nse http-robtex-shared-ns.nse http-sap-netweaver-leak.nse http-security-headers.nse http-server-header.nse http-shellshock.nse http-sitemap-generator.nse http-slowloris-check.nse http-slowloris.nse http-sql-injection.nse http-stored-xss.nse http-svn-enum.nse http-svn-info.nse http-title.nse http-tplink-dir-traversal.nse http-trace.nse http-traceroute.nse http-trane-info.nse http-unsafe-output-escaping.nse http-useragent-tester.nse http-userdir-enum.nse http-vhosts.nse http-virustotal.nse http-vlcstreamer-ls.nse http-vmware-path-vuln.nse http-vuln-cve2006-3392.nse http-vuln-cve2009-3960.nse http-vuln-cve2010-0738.nse http-vuln-cve2010-2861.nse http-vuln-cve2011-3192.nse http-vuln-cve2011-3368.nse http-vuln-cve2012-1823.nse http-vuln-cve2013-0156.nse http-vuln-cve2013-6786.nse http-vuln-cve2013-7091.nse http-vuln-cve2014-2126.nse http-vuln-cve2014-2127.nse http-vuln-cve2014-2128.nse http-vuln-cve2014-2129.nse http-vuln-cve2014-3704.nse http-vuln-cve2014-8877.nse http-vuln-cve2015-1427.nse http-vuln-cve2015-1635.nse http-vuln-cve2017-1001000.nse http-vuln-cve2017-5638.nse http-vuln-cve2017-5689.nse http-vuln-cve2017-8917.nse http-vuln-misfortune-cookie.nse http-vuln-wnr1000-creds.nse http-waf-detect.nse http-waf-fingerprint.nse http-webdav-scan.nse http-wordpress-brute.nse http-wordpress-enum.nse http-wordpress-users.nse http-xssed.nse https-redirect.nse ip-https-discover.nse membase-http-info.nse riak-http-info.nse ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# |
http 관련 스크립트를 전부 실행
nmap –p 80 –sV —script “http-*” 192.168.0.9
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# ls | grep "http-" http-adobe-coldfusion-apsa1301.nse http-affiliate-id.nse http-apache-negotiation.nse http-apache-server-status.nse http-aspnet-debug.nse http-auth-finder.nse http-auth.nse http-avaya-ipoffice-users.nse http-awstatstotals-exec.nse http-axis2-dir-traversal.nse http-backup-finder.nse http-barracuda-dir-traversal.nse http-bigip-cookie.nse http-brute.nse http-cakephp-version.nse http-chrono.nse http-cisco-anyconnect.nse http-coldfusion-subzero.nse http-comments-displayer.nse http-config-backup.nse http-cookie-flags.nse http-cors.nse http-cross-domain-policy.nse http-csrf.nse http-date.nse http-default-accounts.nse http-devframework.nse http-dlink-backdoor.nse http-dombased-xss.nse http-domino-enum-passwords.nse http-drupal-enum-users.nse http-drupal-enum.nse http-enum.nse http-errors.nse http-exif-spider.nse http-favicon.nse http-feed.nse http-fetch.nse http-fileupload-exploiter.nse http-form-brute.nse http-form-fuzzer.nse http-frontpage-login.nse http-generator.nse http-git.nse http-gitweb-projects-enum.nse http-google-malware.nse http-grep.nse http-headers.nse http-hp-ilo-info.nse http-huawei-hg5xx-vuln.nse http-icloud-findmyiphone.nse http-icloud-sendmsg.nse http-iis-short-name-brute.nse http-iis-webdav-vuln.nse http-internal-ip-disclosure.nse http-joomla-brute.nse http-jsonp-detection.nse http-litespeed-sourcecode-download.nse http-ls.nse http-majordomo2-dir-traversal.nse http-malware-host.nse http-mcmp.nse http-method-tamper.nse http-methods.nse http-mobileversion-checker.nse http-ntlm-info.nse http-open-proxy.nse http-open-redirect.nse http-passwd.nse http-php-version.nse http-phpmyadmin-dir-traversal.nse http-phpself-xss.nse http-proxy-brute.nse http-put.nse http-qnap-nas-info.nse http-referer-checker.nse http-rfi-spider.nse http-robots.txt.nse http-robtex-reverse-ip.nse http-robtex-shared-ns.nse http-sap-netweaver-leak.nse http-security-headers.nse http-server-header.nse http-shellshock.nse http-sitemap-generator.nse http-slowloris-check.nse http-slowloris.nse http-sql-injection.nse http-stored-xss.nse http-svn-enum.nse http-svn-info.nse http-title.nse http-tplink-dir-traversal.nse http-trace.nse http-traceroute.nse http-trane-info.nse http-unsafe-output-escaping.nse http-useragent-tester.nse http-userdir-enum.nse http-vhosts.nse http-virustotal.nse http-vlcstreamer-ls.nse http-vmware-path-vuln.nse http-vuln-cve2006-3392.nse http-vuln-cve2009-3960.nse http-vuln-cve2010-0738.nse http-vuln-cve2010-2861.nse http-vuln-cve2011-3192.nse http-vuln-cve2011-3368.nse http-vuln-cve2012-1823.nse http-vuln-cve2013-0156.nse http-vuln-cve2013-6786.nse http-vuln-cve2013-7091.nse http-vuln-cve2014-2126.nse http-vuln-cve2014-2127.nse http-vuln-cve2014-2128.nse http-vuln-cve2014-2129.nse http-vuln-cve2014-3704.nse http-vuln-cve2014-8877.nse http-vuln-cve2015-1427.nse http-vuln-cve2015-1635.nse http-vuln-cve2017-1001000.nse http-vuln-cve2017-5638.nse http-vuln-cve2017-5689.nse http-vuln-cve2017-8917.nse http-vuln-misfortune-cookie.nse http-vuln-wnr1000-creds.nse http-waf-detect.nse http-waf-fingerprint.nse http-webdav-scan.nse http-wordpress-brute.nse http-wordpress-enum.nse http-wordpress-users.nse http-xssed.nse membase-http-info.nse riak-http-info.nse ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# |
NSE 분류
Network discovery
More Sophisticated and accurate OS version detction
기본 NMAP과 비교하여 정밀한 탐지가 가능하다.
3. Vulnerability Detection
4. Backdoor Detection
5. Vulnerability Exploitation ---> #취약점 공격해서 침투테스트까지 가능하다.
NMAP + Script : 정교하거나 추가된 기능을 사용할 수 있다.
Script ---> NMAP에서 사용하는 script의 확장자 : nse
현재 설치된 운영체제에서 nse 파일을 찾아보자.
find / -name *.nse #파일을 찾음.
locate *.nse #파일의 위치를 찾아준다.
nse 스크립트 파일의 위치 : /usr/share/nmap/scripts/
nmap의 스크립트 파일은 업데이트가 가능하다.
nmap --script-update
nmap --script-updatedb
dns-brute.nse ===> 딕셔너리 어택 : 대상 : DNS #루비 코드로 작성되어 있다.
--->dns enum 공격
사용법 : 기본 NMAP
nmap –p 53 —script dns-brute.nse [공격대상 dns서버]
#툴마다 기능이 다르기 때문에 다양하게 사용하고 비교하자.
www.ubiedu.co.kr / 14.36.28.250
--> 버츄얼 호스팅이 되어 있다.
--> 도메인 주소는 https 보안이 되어 있다.
--> IP로 접속 하였을때는 보안이 취약할 수도 있다.
대상 사이트가 웹 서버일 때
http 페이지를 식별한다.
http-enum.nse
nmap —script http-enum.nse 192.168.0.9
스캔 완료 화면
스캐너 : vulscan.nse #취약점 탐색
기본 NSE에는 없음 --> 추가 다운로드 필요
cd /usr/share/nmap/scripts/
mkdir addon
cd addon
wget https://github.com/vulnersCom/nmap-vulners/archive/refs/heads/master.zip
unzip master.zip
nmap-vulners-master/vulners.nse 획득
https://podman.io/ : pod를 적게 사용하는 경우
kubernetes ---> 이름이 갈다. ---> k9s ---> : 구버네티스 오케이스트레이션 프로그램 자체가 무겁다.
-ubernete
==> micro Kuvernetes
--> k9s
웹서버 취약점 분석 (CVE 취약점 분석)
nmap –sV –p 80 —script=nmap-vulners-master/vulners.nse
msfconsole과 연계 가능 #CVE코드 검색
msfconsole
search [CVE코드]
ls | grep ssh
ssh-brute.nse : ssh 서비스에 대한 브루트포스를 진행
필수조건 : user.lst
pw.lst
기본으로 만들어 쓰자.
echo “aaa
bbb
ccc“ > user.lst
echo “aaa
bbb
ccc“ > pw.lst
공격코드
nmap -n -p22 --script ssh-brute.nse --script-args userdb=user.lst,passdb=pw.lst 192.168.0.9
부르트포스 날림
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# nmap -n -p22 --script ssh-brute.nse --script-args userdb=user.lst,passdb=pw.lst 192.168.0.9 Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-30 10:42 KST NSE: [ssh-brute] Trying username/password pair: aaa:aaa NSE: [ssh-brute] Trying username/password pair: bbb:bbb NSE: [ssh-brute] Trying username/password pair: ccc:ccc NSE: [ssh-brute] Trying username/password pair: bbb:aaa NSE: [ssh-brute] Trying username/password pair: ccc:aaa NSE: [ssh-brute] Trying username/password pair: aaa:bbb NSE: [ssh-brute] Trying username/password pair: ccc:bbb NSE: [ssh-brute] Trying username/password pair: aaa:ccc NSE: [ssh-brute] Trying username/password pair: bbb:ccc Nmap scan report for 192.168.0.9 Host is up (0.00024s latency). |
SMB 유저 탐색
smb-enum.nse
nmap –n –p139,445 --script=smb-enum-users --script-args=smbuername=“test”, \smbpassword=“asd123!@”,samronly 192.168.0.9
firewalk.nse (방화벽에 적용된 룰 확인) +@
대상 서버에 설정되어 있는 방화벽 설정값을 확인 ---> port scan
추가 기능 --> traceroute : 경로 확인
nmap --script firewalk.nse --traceroute 192.168.0.9
myspl-info.nse
mysql정보와 버전 상태 // --> password salt : 소금(salt) ---> 패스워드를 알아내기 위한 키 (패스워드)
nmap —script=mysql-info.nse –sV –sC 192.168.0.9
https://st-lab.tistory.com/100
nse파일
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# ls | grep http http-adobe-coldfusion-apsa1301.nse http-affiliate-id.nse http-apache-negotiation.nse http-apache-server-status.nse http-aspnet-debug.nse http-auth-finder.nse http-auth.nse http-avaya-ipoffice-users.nse http-awstatstotals-exec.nse http-axis2-dir-traversal.nse http-backup-finder.nse http-barracuda-dir-traversal.nse http-bigip-cookie.nse http-brute.nse http-cakephp-version.nse http-chrono.nse http-cisco-anyconnect.nse http-coldfusion-subzero.nse http-comments-displayer.nse http-config-backup.nse http-cookie-flags.nse http-cors.nse http-cross-domain-policy.nse http-csrf.nse http-date.nse http-default-accounts.nse http-devframework.nse http-dlink-backdoor.nse http-dombased-xss.nse http-domino-enum-passwords.nse http-drupal-enum-users.nse http-drupal-enum.nse http-enum.nse http-errors.nse http-exif-spider.nse http-favicon.nse http-feed.nse http-fetch.nse http-fileupload-exploiter.nse http-form-brute.nse http-form-fuzzer.nse http-frontpage-login.nse http-generator.nse http-git.nse http-gitweb-projects-enum.nse http-google-malware.nse http-grep.nse http-headers.nse http-hp-ilo-info.nse http-huawei-hg5xx-vuln.nse http-icloud-findmyiphone.nse http-icloud-sendmsg.nse http-iis-short-name-brute.nse http-iis-webdav-vuln.nse http-internal-ip-disclosure.nse http-joomla-brute.nse http-jsonp-detection.nse http-litespeed-sourcecode-download.nse http-ls.nse http-majordomo2-dir-traversal.nse http-malware-host.nse http-mcmp.nse http-method-tamper.nse http-methods.nse http-mobileversion-checker.nse http-ntlm-info.nse http-open-proxy.nse http-open-redirect.nse http-passwd.nse http-php-version.nse http-phpmyadmin-dir-traversal.nse http-phpself-xss.nse http-proxy-brute.nse http-put.nse http-qnap-nas-info.nse http-referer-checker.nse http-rfi-spider.nse http-robots.txt.nse http-robtex-reverse-ip.nse http-robtex-shared-ns.nse http-sap-netweaver-leak.nse http-security-headers.nse http-server-header.nse http-shellshock.nse http-sitemap-generator.nse http-slowloris-check.nse http-slowloris.nse http-sql-injection.nse http-stored-xss.nse http-svn-enum.nse http-svn-info.nse http-title.nse http-tplink-dir-traversal.nse http-trace.nse http-traceroute.nse http-trane-info.nse http-unsafe-output-escaping.nse http-useragent-tester.nse http-userdir-enum.nse http-vhosts.nse http-virustotal.nse http-vlcstreamer-ls.nse http-vmware-path-vuln.nse http-vuln-cve2006-3392.nse http-vuln-cve2009-3960.nse http-vuln-cve2010-0738.nse http-vuln-cve2010-2861.nse http-vuln-cve2011-3192.nse http-vuln-cve2011-3368.nse http-vuln-cve2012-1823.nse http-vuln-cve2013-0156.nse http-vuln-cve2013-6786.nse http-vuln-cve2013-7091.nse http-vuln-cve2014-2126.nse http-vuln-cve2014-2127.nse http-vuln-cve2014-2128.nse http-vuln-cve2014-2129.nse http-vuln-cve2014-3704.nse http-vuln-cve2014-8877.nse http-vuln-cve2015-1427.nse http-vuln-cve2015-1635.nse http-vuln-cve2017-1001000.nse http-vuln-cve2017-5638.nse http-vuln-cve2017-5689.nse http-vuln-cve2017-8917.nse http-vuln-misfortune-cookie.nse http-vuln-wnr1000-creds.nse http-waf-detect.nse http-waf-fingerprint.nse http-webdav-scan.nse http-wordpress-brute.nse http-wordpress-enum.nse http-wordpress-users.nse http-xssed.nse https-redirect.nse ip-https-discover.nse membase-http-info.nse riak-http-info.nse ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# |
http 관련 스크립트를 전부 실행
nmap –p 80 –sV —script “http-*” 192.168.0.9
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# ls | grep "http-" http-adobe-coldfusion-apsa1301.nse http-affiliate-id.nse http-apache-negotiation.nse http-apache-server-status.nse http-aspnet-debug.nse http-auth-finder.nse http-auth.nse http-avaya-ipoffice-users.nse http-awstatstotals-exec.nse http-axis2-dir-traversal.nse http-backup-finder.nse http-barracuda-dir-traversal.nse http-bigip-cookie.nse http-brute.nse http-cakephp-version.nse http-chrono.nse http-cisco-anyconnect.nse http-coldfusion-subzero.nse http-comments-displayer.nse http-config-backup.nse http-cookie-flags.nse http-cors.nse http-cross-domain-policy.nse http-csrf.nse http-date.nse http-default-accounts.nse http-devframework.nse http-dlink-backdoor.nse http-dombased-xss.nse http-domino-enum-passwords.nse http-drupal-enum-users.nse http-drupal-enum.nse http-enum.nse http-errors.nse http-exif-spider.nse http-favicon.nse http-feed.nse http-fetch.nse http-fileupload-exploiter.nse http-form-brute.nse http-form-fuzzer.nse http-frontpage-login.nse http-generator.nse http-git.nse http-gitweb-projects-enum.nse http-google-malware.nse http-grep.nse http-headers.nse http-hp-ilo-info.nse http-huawei-hg5xx-vuln.nse http-icloud-findmyiphone.nse http-icloud-sendmsg.nse http-iis-short-name-brute.nse http-iis-webdav-vuln.nse http-internal-ip-disclosure.nse http-joomla-brute.nse http-jsonp-detection.nse http-litespeed-sourcecode-download.nse http-ls.nse http-majordomo2-dir-traversal.nse http-malware-host.nse http-mcmp.nse http-method-tamper.nse http-methods.nse http-mobileversion-checker.nse http-ntlm-info.nse http-open-proxy.nse http-open-redirect.nse http-passwd.nse http-php-version.nse http-phpmyadmin-dir-traversal.nse http-phpself-xss.nse http-proxy-brute.nse http-put.nse http-qnap-nas-info.nse http-referer-checker.nse http-rfi-spider.nse http-robots.txt.nse http-robtex-reverse-ip.nse http-robtex-shared-ns.nse http-sap-netweaver-leak.nse http-security-headers.nse http-server-header.nse http-shellshock.nse http-sitemap-generator.nse http-slowloris-check.nse http-slowloris.nse http-sql-injection.nse http-stored-xss.nse http-svn-enum.nse http-svn-info.nse http-title.nse http-tplink-dir-traversal.nse http-trace.nse http-traceroute.nse http-trane-info.nse http-unsafe-output-escaping.nse http-useragent-tester.nse http-userdir-enum.nse http-vhosts.nse http-virustotal.nse http-vlcstreamer-ls.nse http-vmware-path-vuln.nse http-vuln-cve2006-3392.nse http-vuln-cve2009-3960.nse http-vuln-cve2010-0738.nse http-vuln-cve2010-2861.nse http-vuln-cve2011-3192.nse http-vuln-cve2011-3368.nse http-vuln-cve2012-1823.nse http-vuln-cve2013-0156.nse http-vuln-cve2013-6786.nse http-vuln-cve2013-7091.nse http-vuln-cve2014-2126.nse http-vuln-cve2014-2127.nse http-vuln-cve2014-2128.nse http-vuln-cve2014-2129.nse http-vuln-cve2014-3704.nse http-vuln-cve2014-8877.nse http-vuln-cve2015-1427.nse http-vuln-cve2015-1635.nse http-vuln-cve2017-1001000.nse http-vuln-cve2017-5638.nse http-vuln-cve2017-5689.nse http-vuln-cve2017-8917.nse http-vuln-misfortune-cookie.nse http-vuln-wnr1000-creds.nse http-waf-detect.nse http-waf-fingerprint.nse http-webdav-scan.nse http-wordpress-brute.nse http-wordpress-enum.nse http-wordpress-users.nse http-xssed.nse membase-http-info.nse riak-http-info.nse ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# |
Network discovery
More Sophisticated and accurate OS version detction
기본 NMAP과 비교하여 정밀한 탐지가 가능하다.
3. Vulnerability Detection
4. Backdoor Detection
5. Vulnerability Exploitation ---> #취약점 공격해서 침투테스트까지 가능하다.
NMAP + Script : 정교하거나 추가된 기능을 사용할 수 있다.
Script ---> NMAP에서 사용하는 script의 확장자 : nse
현재 설치된 운영체제에서 nse 파일을 찾아보자.
find / -name *.nse #파일을 찾음.
locate *.nse #파일의 위치를 찾아준다.
nse 스크립트 파일의 위치 : /usr/share/nmap/scripts/
nmap의 스크립트 파일은 업데이트가 가능하다.
nmap --script-update
nmap --script-updatedb
dns-brute.nse ===> 딕셔너리 어택 : 대상 : DNS #루비 코드로 작성되어 있다.
--->dns enum 공격
사용법 : 기본 NMAP
nmap –p 53 —script dns-brute.nse [공격대상 dns서버]
#툴마다 기능이 다르기 때문에 다양하게 사용하고 비교하자.
www.ubiedu.co.kr / 14.36.28.250
--> 버츄얼 호스팅이 되어 있다.
--> 도메인 주소는 https 보안이 되어 있다.
--> IP로 접속 하였을때는 보안이 취약할 수도 있다.
대상 사이트가 웹 서버일 때
http 페이지를 식별한다.
http-enum.nse
nmap —script http-enum.nse 192.168.0.9
스캔 완료 화면
스캐너 : vulscan.nse #취약점 탐색
기본 NSE에는 없음 --> 추가 다운로드 필요
cd /usr/share/nmap/scripts/
mkdir addon
cd addon
wget https://github.com/vulnersCom/nmap-vulners/archive/refs/heads/master.zip
unzip master.zip
nmap-vulners-master/vulners.nse 획득
https://podman.io/ : pod를 적게 사용하는 경우
kubernetes ---> 이름이 갈다. ---> k9s ---> : 구버네티스 오케이스트레이션 프로그램 자체가 무겁다.
-ubernete
==> micro Kuvernetes
--> k9s
웹서버 취약점 분석 (CVE 취약점 분석)
nmap –sV –p 80 —script=nmap-vulners-master/vulners.nse
msfconsole과 연계 가능 #CVE코드 검색
msfconsole
search [CVE코드]
ls | grep ssh
ssh-brute.nse : ssh 서비스에 대한 브루트포스를 진행
필수조건 : user.lst
pw.lst
기본으로 만들어 쓰자.
echo “aaa
bbb
ccc“ > user.lst
echo “aaa
bbb
ccc“ > pw.lst
공격코드
nmap -n -p22 --script ssh-brute.nse --script-args userdb=user.lst,passdb=pw.lst 192.168.0.9
부르트포스 날림
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# nmap -n -p22 --script ssh-brute.nse --script-args userdb=user.lst,passdb=pw.lst 192.168.0.9 Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-30 10:42 KST NSE: [ssh-brute] Trying username/password pair: aaa:aaa NSE: [ssh-brute] Trying username/password pair: bbb:bbb NSE: [ssh-brute] Trying username/password pair: ccc:ccc NSE: [ssh-brute] Trying username/password pair: bbb:aaa NSE: [ssh-brute] Trying username/password pair: ccc:aaa NSE: [ssh-brute] Trying username/password pair: aaa:bbb NSE: [ssh-brute] Trying username/password pair: ccc:bbb NSE: [ssh-brute] Trying username/password pair: aaa:ccc NSE: [ssh-brute] Trying username/password pair: bbb:ccc Nmap scan report for 192.168.0.9 Host is up (0.00024s latency). |
SMB 유저 탐색
smb-enum.nse
nmap –n –p139,445 --script=smb-enum-users --script-args=smbuername=“test”, \smbpassword=“asd123!@”,samronly 192.168.0.9
firewalk.nse (방화벽에 적용된 룰 확인) +@
대상 서버에 설정되어 있는 방화벽 설정값을 확인 ---> port scan
추가 기능 --> traceroute : 경로 확인
nmap --script firewalk.nse --traceroute 192.168.0.9
myspl-info.nse
mysql정보와 버전 상태 // --> password salt : 소금(salt) ---> 패스워드를 알아내기 위한 키 (패스워드)
nmap —script=mysql-info.nse –sV –sC 192.168.0.9
https://st-lab.tistory.com/100
nse파일
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# ls | grep http http-adobe-coldfusion-apsa1301.nse http-affiliate-id.nse http-apache-negotiation.nse http-apache-server-status.nse http-aspnet-debug.nse http-auth-finder.nse http-auth.nse http-avaya-ipoffice-users.nse http-awstatstotals-exec.nse http-axis2-dir-traversal.nse http-backup-finder.nse http-barracuda-dir-traversal.nse http-bigip-cookie.nse http-brute.nse http-cakephp-version.nse http-chrono.nse http-cisco-anyconnect.nse http-coldfusion-subzero.nse http-comments-displayer.nse http-config-backup.nse http-cookie-flags.nse http-cors.nse http-cross-domain-policy.nse http-csrf.nse http-date.nse http-default-accounts.nse http-devframework.nse http-dlink-backdoor.nse http-dombased-xss.nse http-domino-enum-passwords.nse http-drupal-enum-users.nse http-drupal-enum.nse http-enum.nse http-errors.nse http-exif-spider.nse http-favicon.nse http-feed.nse http-fetch.nse http-fileupload-exploiter.nse http-form-brute.nse http-form-fuzzer.nse http-frontpage-login.nse http-generator.nse http-git.nse http-gitweb-projects-enum.nse http-google-malware.nse http-grep.nse http-headers.nse http-hp-ilo-info.nse http-huawei-hg5xx-vuln.nse http-icloud-findmyiphone.nse http-icloud-sendmsg.nse http-iis-short-name-brute.nse http-iis-webdav-vuln.nse http-internal-ip-disclosure.nse http-joomla-brute.nse http-jsonp-detection.nse http-litespeed-sourcecode-download.nse http-ls.nse http-majordomo2-dir-traversal.nse http-malware-host.nse http-mcmp.nse http-method-tamper.nse http-methods.nse http-mobileversion-checker.nse http-ntlm-info.nse http-open-proxy.nse http-open-redirect.nse http-passwd.nse http-php-version.nse http-phpmyadmin-dir-traversal.nse http-phpself-xss.nse http-proxy-brute.nse http-put.nse http-qnap-nas-info.nse http-referer-checker.nse http-rfi-spider.nse http-robots.txt.nse http-robtex-reverse-ip.nse http-robtex-shared-ns.nse http-sap-netweaver-leak.nse http-security-headers.nse http-server-header.nse http-shellshock.nse http-sitemap-generator.nse http-slowloris-check.nse http-slowloris.nse http-sql-injection.nse http-stored-xss.nse http-svn-enum.nse http-svn-info.nse http-title.nse http-tplink-dir-traversal.nse http-trace.nse http-traceroute.nse http-trane-info.nse http-unsafe-output-escaping.nse http-useragent-tester.nse http-userdir-enum.nse http-vhosts.nse http-virustotal.nse http-vlcstreamer-ls.nse http-vmware-path-vuln.nse http-vuln-cve2006-3392.nse http-vuln-cve2009-3960.nse http-vuln-cve2010-0738.nse http-vuln-cve2010-2861.nse http-vuln-cve2011-3192.nse http-vuln-cve2011-3368.nse http-vuln-cve2012-1823.nse http-vuln-cve2013-0156.nse http-vuln-cve2013-6786.nse http-vuln-cve2013-7091.nse http-vuln-cve2014-2126.nse http-vuln-cve2014-2127.nse http-vuln-cve2014-2128.nse http-vuln-cve2014-2129.nse http-vuln-cve2014-3704.nse http-vuln-cve2014-8877.nse http-vuln-cve2015-1427.nse http-vuln-cve2015-1635.nse http-vuln-cve2017-1001000.nse http-vuln-cve2017-5638.nse http-vuln-cve2017-5689.nse http-vuln-cve2017-8917.nse http-vuln-misfortune-cookie.nse http-vuln-wnr1000-creds.nse http-waf-detect.nse http-waf-fingerprint.nse http-webdav-scan.nse http-wordpress-brute.nse http-wordpress-enum.nse http-wordpress-users.nse http-xssed.nse https-redirect.nse ip-https-discover.nse membase-http-info.nse riak-http-info.nse ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# |
http 관련 스크립트를 전부 실행
nmap –p 80 –sV —script “http-*” 192.168.0.9
| ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# ls | grep "http-" http-adobe-coldfusion-apsa1301.nse http-affiliate-id.nse http-apache-negotiation.nse http-apache-server-status.nse http-aspnet-debug.nse http-auth-finder.nse http-auth.nse http-avaya-ipoffice-users.nse http-awstatstotals-exec.nse http-axis2-dir-traversal.nse http-backup-finder.nse http-barracuda-dir-traversal.nse http-bigip-cookie.nse http-brute.nse http-cakephp-version.nse http-chrono.nse http-cisco-anyconnect.nse http-coldfusion-subzero.nse http-comments-displayer.nse http-config-backup.nse http-cookie-flags.nse http-cors.nse http-cross-domain-policy.nse http-csrf.nse http-date.nse http-default-accounts.nse http-devframework.nse http-dlink-backdoor.nse http-dombased-xss.nse http-domino-enum-passwords.nse http-drupal-enum-users.nse http-drupal-enum.nse http-enum.nse http-errors.nse http-exif-spider.nse http-favicon.nse http-feed.nse http-fetch.nse http-fileupload-exploiter.nse http-form-brute.nse http-form-fuzzer.nse http-frontpage-login.nse http-generator.nse http-git.nse http-gitweb-projects-enum.nse http-google-malware.nse http-grep.nse http-headers.nse http-hp-ilo-info.nse http-huawei-hg5xx-vuln.nse http-icloud-findmyiphone.nse http-icloud-sendmsg.nse http-iis-short-name-brute.nse http-iis-webdav-vuln.nse http-internal-ip-disclosure.nse http-joomla-brute.nse http-jsonp-detection.nse http-litespeed-sourcecode-download.nse http-ls.nse http-majordomo2-dir-traversal.nse http-malware-host.nse http-mcmp.nse http-method-tamper.nse http-methods.nse http-mobileversion-checker.nse http-ntlm-info.nse http-open-proxy.nse http-open-redirect.nse http-passwd.nse http-php-version.nse http-phpmyadmin-dir-traversal.nse http-phpself-xss.nse http-proxy-brute.nse http-put.nse http-qnap-nas-info.nse http-referer-checker.nse http-rfi-spider.nse http-robots.txt.nse http-robtex-reverse-ip.nse http-robtex-shared-ns.nse http-sap-netweaver-leak.nse http-security-headers.nse http-server-header.nse http-shellshock.nse http-sitemap-generator.nse http-slowloris-check.nse http-slowloris.nse http-sql-injection.nse http-stored-xss.nse http-svn-enum.nse http-svn-info.nse http-title.nse http-tplink-dir-traversal.nse http-trace.nse http-traceroute.nse http-trane-info.nse http-unsafe-output-escaping.nse http-useragent-tester.nse http-userdir-enum.nse http-vhosts.nse http-virustotal.nse http-vlcstreamer-ls.nse http-vmware-path-vuln.nse http-vuln-cve2006-3392.nse http-vuln-cve2009-3960.nse http-vuln-cve2010-0738.nse http-vuln-cve2010-2861.nse http-vuln-cve2011-3192.nse http-vuln-cve2011-3368.nse http-vuln-cve2012-1823.nse http-vuln-cve2013-0156.nse http-vuln-cve2013-6786.nse http-vuln-cve2013-7091.nse http-vuln-cve2014-2126.nse http-vuln-cve2014-2127.nse http-vuln-cve2014-2128.nse http-vuln-cve2014-2129.nse http-vuln-cve2014-3704.nse http-vuln-cve2014-8877.nse http-vuln-cve2015-1427.nse http-vuln-cve2015-1635.nse http-vuln-cve2017-1001000.nse http-vuln-cve2017-5638.nse http-vuln-cve2017-5689.nse http-vuln-cve2017-8917.nse http-vuln-misfortune-cookie.nse http-vuln-wnr1000-creds.nse http-waf-detect.nse http-waf-fingerprint.nse http-webdav-scan.nse http-wordpress-brute.nse http-wordpress-enum.nse http-wordpress-users.nse http-xssed.nse membase-http-info.nse riak-http-info.nse ┌──(root㉿Red)-[/usr/share/nmap/scripts] └─# |
'Kali Linux' 카테고리의 다른 글
| SQLmap (0) | 2023.07.24 |
|---|---|
| kali - Scanner (0) | 2023.07.11 |
| ping scan / proxy 레지트스트 만들기 (0) | 2023.07.10 |
| kali nmap / Ettercap (0) | 2023.07.06 |
| 모의해킹 진행순서 / Kali Linux 정리 (0) | 2023.07.04 |
